The command design pattern is one of the behavioral design patterns. This design pattern can be considered for use when there is clear segregation between requester and executor of an


The command design pattern is one of the behavioral design patterns. This design pattern can be considered for use when there is clear segregation between requester and executor of an

In this article, we will see how to run any task or a program using Spring Scheduled Tasks. As usual, we will demonstrate this with our favorite Spring Boot Softwares

One of the best capabilities of Force.com platform is Salesforce Sandbox, which allows us to create a copy of our production organization. In this article of our Salesforce Learning, we
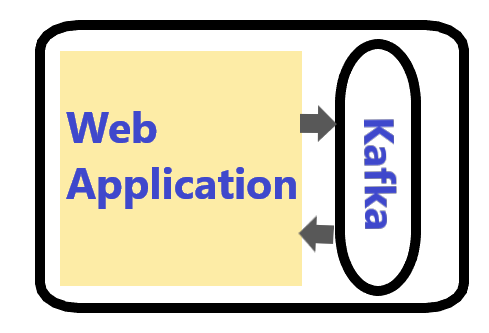
In this article, we will create a simple Message Driven Application using Apache Kafka and Spring Boot. We have already seen how we connect to Kafka using plain java clients. In this
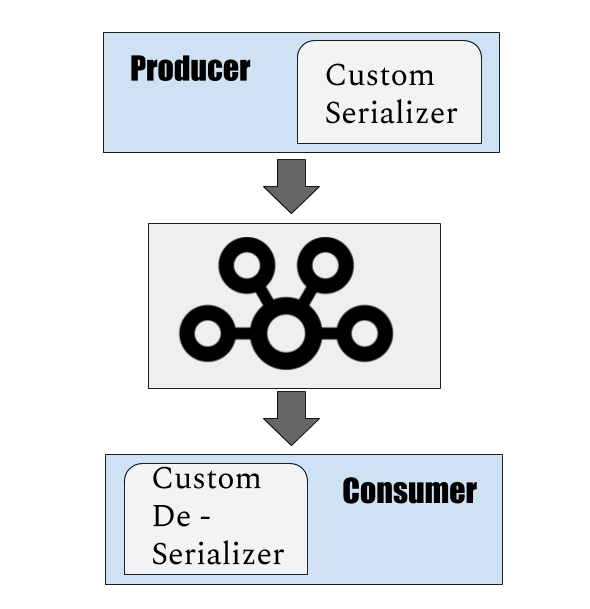
In our last article on implementation of Apache Kafka, we have seen the basic Java client to produce and consume messages. To continue our learning lets see how we can

Every now and then the webmaster has to update his site. He will delete some non performing posts, pages or he will change some categories. While doing this he has
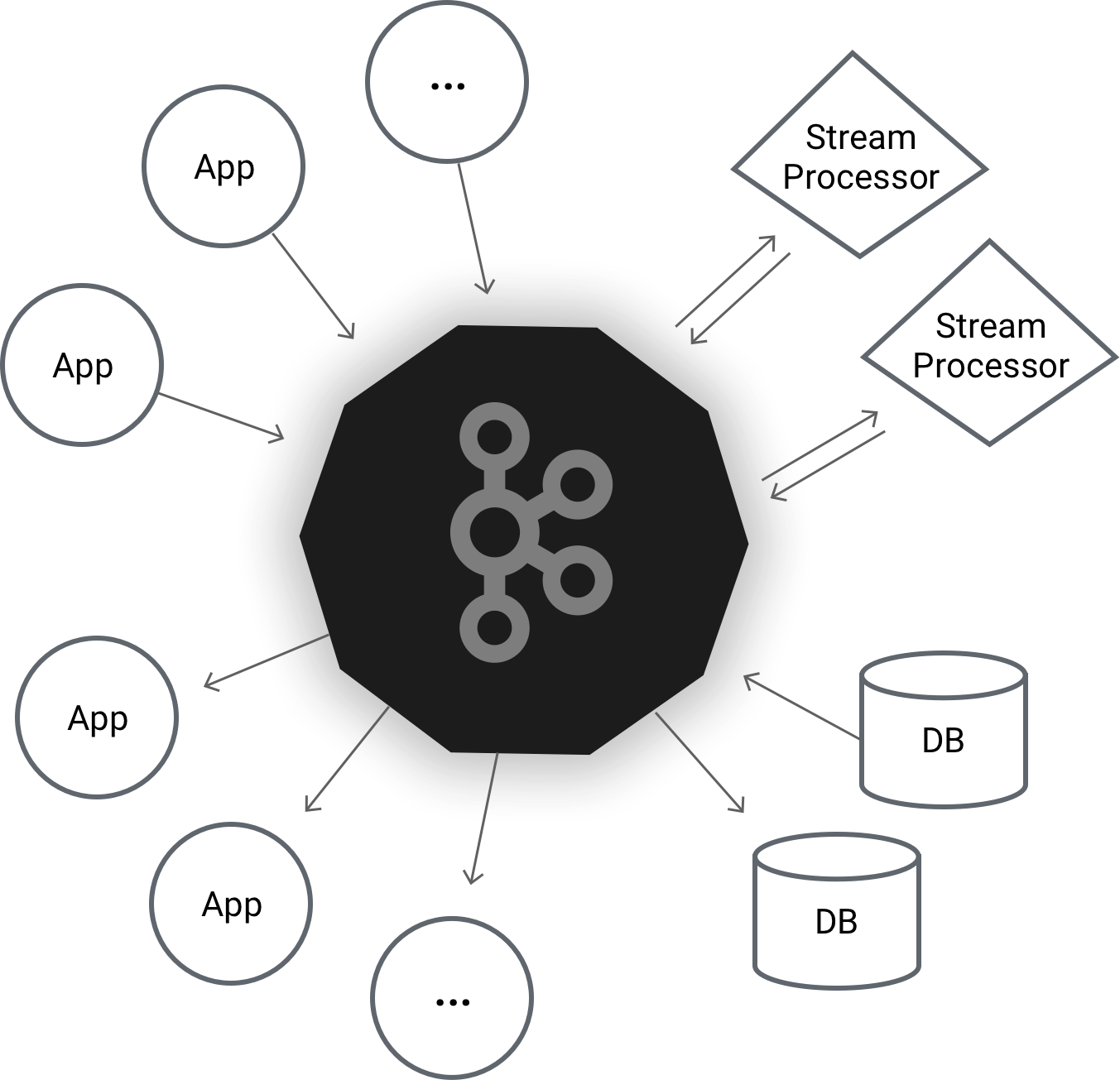
Implement Kafka with Java: Apache Kafka is the buzz word today. Everyone talks about it writes about it. So I have also decided to dive into it and understand it.
Application properties are part of each and every application. To make your project robust and easy for the configuration you always think of keeping some properties either in the file,
Consuming a rest web service is easy and with RestTemplate Spring has made dealing with these rest services easier. In this article we will build a simple Currency Conversion App that uses

Visualforce is nothing but one of the framework of Force.com which is component-based user interface. A tag based language more similar to HTML is used by visualforce. Each tag corresponds

Emails are used as communication modes most of the time. Not always people use encrypted email when sending business-sensitive information. Outlook and other email clients have inbuilt support for this
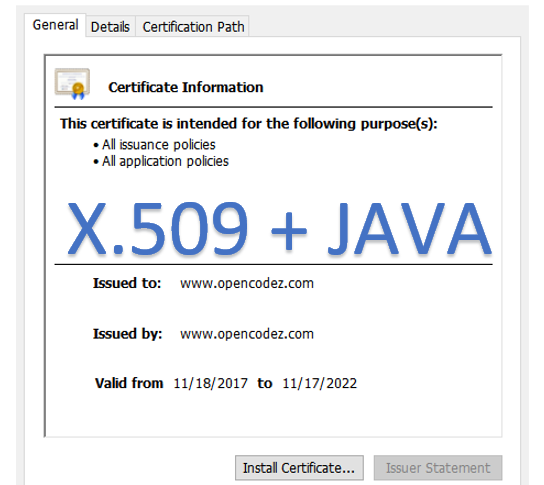
In the NEW IT age with lots of data comes great responsibility to protect it against all malicious attacks. Using secure communications or HTTPS is one of the ways to